such as peak bandwidth, latency, and delay variation when the link is
established between two Bluetooth units.
Host Controller Interface
This is the optional interface layer, provided between the higher (above LMP)
and lower layers of the Bluetooth protocol stack, for accessing the Bluetooth
hardware capabilities. Whenever the higher layers are implemented on the
motherboard of a host device, this layer is needed. Such an approach could
prove beneficial as the spare capacity of the host device (say, a personal
computer) could be utilized. The specification defines details such as the
different packet types as seen by this layer. Command packets that are used by
the host to control the device, event packets that are used by the device to
inform the host of the changes, and data packets come under this category.
2.5.3 Middleware Protocol Group
The basic functionality of the middleware protocol group is to present to the
application layers a standard interface that may be used for communicating
across the transport layer, that is, the applications need not know the transport
layer's complexities, they can just use the application programming
interfaces(APIs) or higher level functions provided by the middleware
protocols. This group consists of the RFCOMM layer, service discovery
protocol (SDP), IrDA interoperability protocols, telephony control specification
(TCS), and audio. The RFCOMM layer presents a virtual serial port to
applications using the serial interface. Any application which is using the serial
port can work seamlessly on Bluetooth devices. RFCOMM uses an L2CAP
connection to establish a link between two devices. In the case of Bluetooth
devices, there is no device which will be static and hence services offered by the
other devices have to be discovered. This is achieved by using the service
discovery protocol (SDP) of the Bluetooth protocol stack. Service discovery
makes the device self configured without manual intervention. The IrDA
interoperability protocol is not for communication between Bluetooth devices
and Infrared devices. It is only for the existing IrDA applications to work on
Bluetooth devices without any changes. The main protocols in the IrDA set are
IrOBEX (IrDA object exchange) for exchanging objects between two devices
and IrMC (infrared mobile communications) for synchronization. Audio is the
distinguishing part of Bluetooth. Audio is given the highest priority and is
directly carried over the baseband at 64 Kbps so that a very good quality of
voice is provided. Another important point to note here is that audio is actually
not a layer of the protocol stack, but only a specific packet format that can be
transmitted directly over the SCO links of the baseband layer. Telephony
control is implemented using the telephony control specification –binary (TCS�
BIN) protocol. TCS defines three major functional areas: call control, group
management, and connectionless TCS. Call control is used to setup calls which
can be subsequently used to carry voice and data traffic. TCS operates in both
point-to-point and point-to-multipoint configurations. One of the main concepts
of TCS is that of the wireless user group (WUG). Group management enables
multiple telephone extensions, call forwarding, and group calls. For example,
consider multiple handsets and a single base set. When a call comes in to the
base set, all the multiple handsets can receive this call. In a similar fashion, calls
can also be forwarded. The functionalities of TCS include configuration
distribution and fastintermember access. Configuration distribution is the
mechanism used to find the information about the other members in a group.
Fast inter member access is a method for two slaves to create a new piconet.
AWUG member uses the information from the configuration distribution and
determines another member which it wants to contact. Then it sends the device's
information to the master, which forwards it to this device. The contacted device
then responds with its device address and clock information and places itself in
a page scan state. Then the master contacts the device initiating the
communication. This device now pages the contacted device and forms a new
piconet. This explains how a new piconet is formed between two slaves with the
help of the master. In all the above cases, a connection-oriented channel is
established. To exchange simple information such as adjusting volume or
signaling information, establishing such a channel is overkill and hence
connectionless TCS has been provided for having a connectionless channel.
1.5.4 Bluetooth Profiles
These profiles have been developed to promote interoperability among the many
implementations of the Bluetooth protocol stack. Each Bluetooth profile
specification has been defined to provide a clear and transparent standard that
can be used to implement a specific user end function. Two Bluetooth devices
can achieve a common functionality only if both devices support identical
profiles. For example, a cellular phone and a headset both have to support the
Bluetooth headset profile for the headset to work with the phone. The Bluetooth
profiles spring up from the usage models. In all, 13 profiles have been listed and
these can be broadly classified into the following four categories:
1. Generic profiles: The Generic access profile, which is not really an
application, provides a way to establish and maintain secure links between the
master and the slaves. The service discovery profile enables users to access SDP
to find out which applications (Bluetooth services)are supported by a specific
device.
2. Telephony profiles: The cordless telephony profile is designed for three in�
one phones. The Intercom profile supports two-way voice communication
between two Bluetooth devices within range of each other. The Headset profile
specifies how Bluetooth can provide a wireless connection to a headset (with
earphones/microphones) for use with a computer or a mobile phone.
3. Networking profiles: The LAN Access profile enables Bluetooth devices to
either connect to a LAN through APs or form a small wireless LAN among
themselves. The dial-up networking profile is designed to provide dial-up
connections via Bluetooth-enabled mobile phones. The FAX profile, very
similar to the dial-up networking profile, enables computers to send and receive
faxes via a Bluetooth-enabled mobile phone.
4. Serial and object exchange profiles: The serial port profile emulates a serial
line (RS232 and USB serial ports) for (legacy) applications that require a serial
line. The other profiles, generic object exchange, object push, file transfer, and
synchronization, are for exchanging objects between two wireless devices.
Bluetooth is the first wireless technology which has actually tried to attempt to
make all the household consumer electronics devices follow one particular
communication paradigm. It has been partially successful, but it does have its
limitations. Bluetooth communication currently does not provide support for
routing. It should be noted that some research efforts are under way to
accommodate this in the Bluetooth specification. Once the routing provision is
given, inter-piconet communication could be enhanced. The issues of handoffs
also have not yet been dealt with till now. Although master–slave architecture
has aided low cost, the master becomes the bottleneck for the whole piconet in
terms of performance, fault tolerance, and bandwidth utilization. Most
importantly, Bluetooth communication takes place in the same frequency band
as that of WLAN and hence robust coexistence solutions need to be developed
to avoid interference. The technology is still under development. Currently,
there are nearly 1,800 adopter companies which are contributing toward the
development of the technology.
1.6 HOME RF
Wireless home networking represents the use of the radio frequency
(RF)spectrum to transmit voice and data in confined areas such as homes and
small offices. One of the visionary concepts that home networking intends to
achieve is the establishment of communication between home appliances such
as computers, TVs, telephones, refrigerators, and air conditioners. Wireless
home networks have an edge over their wired counterparts because features
such as flexibility (enabling of file and drive sharing) and interoperability that
exist in the wired networks are coupled with those in the wireless domain,
namely, simplicity of installation and mobility. The HIPERLAN/2, as
mentioned earlier, has provisions for direct communication between the mobile
terminals (the home environment). The home environment enables election of a
central controller (CC) which coordinates the communication process. This
environment is helpful in setting up home networks. Apart from this, an industry
consortium known as the Home RF Working Group has developed a technology
that is termed HomeRF. This technology intends to integrate devices used in
homes into a single network and utilize RF links for communication. HomeRF
is a strong competitor to Bluetooth as it operates in the ISM band.
Technical Features The HomeRF provides data rates of 1.6 Mbps, a little
higher than the Bluetooth rate, supporting both infrastructure-based and ad hoc
communications. It provides a guaranteed QoS delivery to voice-only devices
and best-effort delivery for data-only devices. The devices need to be plug-and�
play enabled; this needs automatic device discovery and identification in the
network. Atypical HomeRF network consists of resource providers (through
which communication to various resources such as the cable modem and phone
lines is effected), and the devices connected to them (such as the cordless
phone, printers, and file servers). The HomeRF technology follows a protocol
called the shared wireless access protocol (SWAP). The protocol is used to set
up a network that provides access to a public network telephone, the Internet
(data), entertainment networks (cable television, digital audio, and video),
transfer and sharing of data resources (such as disks and printers), and home
control and automation. The SWAP has been derived from the IEEE 802.11 and
the European digitally enhanced cordless telephony (DECT) standards. It
employs a hybrid TDMA/CSMA scheme for channel access. While TDMA
handles isochronous transmission (similar to synchronous transmission,
isochronous transmission is also used for multimedia communication where
both the schemes have stringent timing constraints, but isochronous
transmission is not as rigid as synchronous transmission in which data streams
are delivered only at specific intervals), CSMA supports asynchronous
transmission (in a manner similar to that of the IEEE 802.11 standard), thereby
making the actual framing structure more complex. The SWAP, however,
differs from the IEEE 802.11specification by not having the RTS-CTS
handshake since it is more economical to do away with the expensive
handshake; moreover, the hidden terminal problem does not pose a serious
threat in the case of small-scale networks such as the home networks. The
SWAP can support up to 127 devices, each identified uniquely by a 48-
bitnetwork identifier. The supported devices can fall into one (or more) of the
following four basic types:
• Connection point that provides a gateway to the public switched telephone
network (PSTN), hence supporting voice and data services.
• Asynchronous data node that uses the CSMA/CA mechanism to communicate
with other nodes.
• Voice node that uses TDMA for communication.
• Voice and data node that can use both CSMA/CA and TDMA for channel
access. Home networking also needs strong security measures to safeguard
against potential eavesdroppers. That is the reason why SWAP uses strong
algorithms such as Blowfish encryption. HomeRF also includes support for
optional packet compression which provides a trade-off between bandwidth and
power consumption. Because of its complex (hybrid) MAC and higher
capability physical layer, the cost of HomeRF devices is higher than that of
Bluetooth devices. HomeRF Version 2.0, released recently, offers higher data
rates (up to 10 Mbps by using wider channels in the ISM band through FHSS).
Infrared The infrared technology (IrDA) uses the infrared region of the light for
communication . Some of the characteristics of these communications are as
follows:
• The infrared rays can be blocked by obstacles, such as walls and buildings.
• The effective range of infrared communications is about one meter. But when
high power is used, it is possible to achieve better ranges.
• The power consumed by infrared devices is extremely low.
• Data rates of 4 Mbps are easily achievable using infrared communications.
• The cost of infrared devices is very low compared to that of Bluetooth devices.
Although the restriction of line of sight (LoS) is there on the infrared devices,
they are extremely popular because they are cheap and consume less power. The
infrared technology has been prevalent for a longer time than Bluetooth wireless
communications. So it has more widespread usage than Bluetooth. Table1.2
compares the technical features of Bluetooth, HomeRF, and IrDAtechnologies.
Table 1.2. Illustrative comparison among Bluetooth, HomeRF, and IrDA
technologies
**** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** ****
MULTIPLE ACCESS TECHNIQUES
In wireless communication systems, it is often desirable to allow the subscriber to
send information simultaneously from the mobile station to the base station while
receiving information from the base station to the mobile station.
A cellular system divides any given area into cells where a mobile unit in each cell
communicates with a base station. The main aim in the cellular system design is to
be able to increase the capacity of the channel, i.e., to handle as many calls as
possible in a given bandwidth with a sufficient level of quality of service.
There are several different ways to allow access to the channel. These includes
mainly the following –
Frequency division multiple-access (FDMA)
Time division multiple-access (TDMA)
Code division multiple-access (CDMA)
Space division multiple access (SDMA)
Depending on how the available bandwidth is allocated to the users, these
techniques can be classified as narrowband and wideband systems.
Narrowband Systems
Systems operating with channels substantially narrower than the coherence
bandwidth are called as Narrow band systems. Narrow band TDMA allows users to
use the same channel but allocates a unique time slot to each user on the channel,
thus separating a small number of users in time on a single channel.
Wideband Systems
In wideband systems, the transmission bandwidth of a single channel is much larger
than the coherence bandwidth of the channel. Thus, multipath fading doesn’t greatly
affect the received signal within a wideband channel, and frequency selective fades
occur only in a small fraction of the signal bandwidth.
FREQUENCY DIVISION MULTIPLE ACCESS (FDMA)
FDMA is the basic technology for advanced mobile phone services. The features of
FDMA are as follows.
FDMA allots a different sub-band of frequency to each different user to access the
network.
If FDMA is not in use, the channel is left idle instead of allotting to the other users.
FDMA is implemented in Narrowband systems and it is less complex than TDMA.
Tight filtering is done here to reduce adjacent channel interference.
The base station BS and mobile station MS, transmit and receive simultaneously
and continuously in FDMA.
FDMA is different from frequency division duplexing (FDD).
While FDMA permits multiple users to simultaneously access a transmission system, FDD describes the way the radio channel is shared between the downlink and uplink.
FDMA is also different from Frequency-division multiplexing (FDM). FDM refers to a
physical layer method that blends and transmits low-bandwidth channels via a high�
bandwidth channel. FDMA, in contrast, is a channel access technique in the data link
layer.
TIME DIVISION MULTIPLE ACCESS (TDMA)
In the cases where continuous transmission is not required, there TDMA is used
instead of FDMA. The features of TDMA include the following.
TDMA shares a single carrier frequency with several users where each users
makes use of non overlapping time slots.
Data transmission in TDMA is not continuous, but occurs in bursts. Hence handsoff
process is simpler.
TDMA uses different time slots for transmission and reception thus duplexers are
not required.
TDMA has an advantage that is possible to allocate different numbers of time slots
per frame to different users.
Bandwidth can be supplied on demand to different users by concatenating or
reassigning time slot based on priority.Time Division Multiple Access (TDMA) is a digital cellular telephone communication technology. It facilitates many users to share the same frequency without interference. Its technology divides a signal into different timeslots, and increases the data carrying capacity.
Time Division Multiple Access (TDMA) is a complex technology, because it requires
an accurate synchronization between the transmitter and the receiver. TDMA is used
in digital mobile radio systems. The individual mobile stations cyclically assign a
frequency for the exclusive use of a time interval.
In most of the cases, the entire system bandwidth for an interval of time is not
assigned to a station. However, the frequency of the system is divided into sub�
bands, and TDMA is used for the multiple access in each sub-band. Sub-bands are
known as carrier frequencies. The mobile system that uses this technique is referred
as the multi-carrier systems.
CODE DIVISION MULTIPLE ACCESS (CDMA)
Code division multiple access technique is an example of multiple access where
several transmitters use a single channel to send information simultaneously. Its
features are as follows.
In CDMA every user uses the full available spectrum instead of getting allotted by
separate frequency.
CDMA is much recommended for voice and data communications.
While multiple codes occupy the same channel in CDMA, the users having same
code can communicate with each other.
CDMA offers more air-space capacity than TDMA.
The hands-off between base stations is very well handled by CDMA.Code Division Multiple Access (CDMA) is a sort of multiplexing that facilitates
various signals to occupy a single transmission channel. It optimizes the use of
available bandwidth. The technology is commonly used in ultra-high-frequency
(UHF) cellular telephone systems, bands ranging between the 800-MHz and 1.9-GHz.
SPACE DIVISION MULTIPLE ACCESS (SDMA)
Space division multiple access or spatial division multiple access is a technique
which is MIMO (multiple-input multiple-output) architecture and used mostly in
wireless and satellite communication. It has the following features.
All users can communicate at the same time using the same channel.
SDMA is completely free from interference.
A single satellite can communicate with more satellites receivers of the same
frequency.
The directional spot-beam antennas are used and hence the base station in SDMA,
can track a moving user.
Controls the radiated energy for each user in space.
Space-division multiple access (SDMA) is a channel access method based on
creating parallel spatial pipes (focused signal beams) using advanced antenna
technology next to higher capacity pipes through spatial multiplexing and/or diversity,
by which it is able to offer superior performance in radio multiple access
communication systems (where multiple users may need to use the communication
media simultaneously)
In traditional mobile cellular network systems, the base station has no information on
the position of the mobile units within the cell and radiates the signal in all directions
within the cell in order to provide radio coverage. This method results in wasting
power on transmissions when there are no mobile units to reach, in addition to
causing interference for adjacent cells using the same frequency, so called co�
channel cells. Likewise, in reception, the antenna receives signals coming from all
directions including noise and interference signals.
By using smart antenna technology and differing spatial locations of mobile units within the cell, space� division multiple access techniques offer attractive performance enhancements. The radiation pattern of the base station, both in transmission and reception, is adapted
to each user to obtain highest gain in the direction of that user. This is often done
using phased array techniques.
********************************************************************
********************************************************************
SPREAD SPECTRUM MODULATION
Introduction:
Initially developed for military applications during II world war, that was less sensitive
to intentional interference or jamming by third parties. Spread spectrum technology has
blossomed into one of the fundamental building blocks in current and next-generation
wireless systems.
Problem of radio transmission
Narrow band can be wiped out due to interference. To disrupt the communication,
the adversary needs to do two things,
(a) to detect that a transmission is taking place and
(b) to transmit a jamming signal which is designed to confuse the receiver.
Solution
A spread spectrum system is therefore designed to make these tasks as difficult
as possible.
Firstly, the transmitted signal should be difficult to detect by an adversary/jammer,
i.e., the signal should have a low probabilityof intercept (LPI).
Secondly, the signal should be difficult to disturb with a jamming signal, i.e., the
transmitted signal should possess an anti-jamming (AJ) property
Remedy
spread the narrow band signal into a broad band to protect against
interference
In a digital communication system the primary resources are Bandwidth and
Power. The study of digital communication system deals with efficient utilization of
these two resources, but there are situations where it is necessary to sacrifice their
efficient utilization in order to meet certain other design objectives.
For example to provide a form of secure communication (i.e. the transmitted
signal is not easily detected or recognized by unwanted listeners) the bandwidth of the
transmitted signal is increased in excess of the minimum bandwidth necessary to
transmit it. This requirement is catered by a technique known as “Spread Spectrum
Modulation”.
The primary advantage of a Spread – Spectrum communication system is its
ability to reject ‘Interference’ whether it be the unintentional or the intentional
interference.
The definition of Spread – Spectrum modulation may be stated in two parts.
1. Spread Spectrum is a mean of transmission in which the data sequence
occupies a BW (Bandwidth) in excess of the minimum BW necessary to transmit it.
2. The Spectrum Spreading is accomplished before transmission through the use of
a code that is independent of the data sequence. The Same code is used in the receiver to despread the received signal so that the original data sequence may be recovered.
Fig. Block diagram for spread spectrum communication
Fig: Spread spectrum technique.
b(t) = Data Sequence to be transmitted (Narrow Band);
c(t) = Wide Band code ;
s(t) = c(t) * b(t) – (wide Band)
Fig: Spectrum of signal before & after spreading
PSUEDO-NOISE SEQUENCE:
Generation of PN sequence:
Fig: Maximum-length sequence generator for n=3
A feedback shift register is said to be Linear when the feedback logic consists of
entirely mod-2-address (Ex-or gates). In such a case, the zero state is not permitted.
The period of a PN sequence produced by a linear feedback shift register with ‘n’ flip
flops cannot exceed 2^n-1.
When the period is exactly 2^n-1, the PN sequence is called a ‘maximum length
sequence’ or ‘m-sequence’..
Example1: Consider the linear feedback shift register shown in above figure
Involve three flip-flops. The input so is equal to the mod-2 sum of S1 and S3. If
the initial state of the shift register is 100. Then the succession of states will be as
follows.
100,110,011,011,101,010,001,100 . . . . . .
The output sequence (output S3) istherefore. 00111010..........Which repeats itself with
period 23–1 = 7 (n=3). Maximal length codes are commonly used PN codes In binary
shift register, the maximum length sequence is
N = 2m-1
chips, where m is the number of stages of flip-flops in the shift register.
At each clock pulse
• Contents of register shifts one bitright.
• Contents of required stages are modulo 2 added and fed back to input.
Fig: Initial stages of Shift registers 1000
Let initial status of shift register be 1000
Properties of PN Sequence
Randomness of PN sequence is tested byfollowing properties
1. Balance property
2. Run length property
3. Autocorrelation property
1. Balance property
In each Period of the sequence , number of binary ones differ from binary zeros by
at most one digit.
Consider output of shift register 0 0 0 1 0 0 1 1 0 1 0 1 1 1 1
Seven zeros and eight ones -meets balance condition.
2. Run length property
Among the runs of ones and zeros in each period, it is desirable that about one
half the runs of each type are of length 1, one- fourth are of length 2 and one-eighth
are of length 3 and so-on.
Consider output of shift register
Number of runs =8
0 0 0 1 0 0 1 1 0 1 0 1 1 1 1
3 1 2 2 1 1 1 4
3. Auto correlation property
Auto correlation function of a maximal length sequence is periodic and binary
valued. Autocorrelation sequence of binary sequence in polar format is given by
1
= −
=1
Where N is length or the period of the sequence, k is the lag of auto correlation function.
1 = 1
=
− 1 ≠ 1
Where 1 is any Integer. We can also state the auto correlation function is
1
=
{ No. of agreements – No. of disagreements in comparison of one full period }
Consider output of shift register for l=1
= 1/15 * 7 - 8 = -1/15
Yields PN autocorrelation as
Range of PN Sequence Lengths
Length 0f Shift Register, m PN Sequence Length,
7 127
8 255
9 511
10 1023
11 2047
12 4095
13 8191
17 131071
19 524287
Notion of Spread Spectrum:
An important attribute of Spread Spectrum modulation is that it can provide
protection against externally generated interfacing signals with finite power. Protection
against jamming (interfacing) waveforms is provided by purposely making the
information – bearing signal occupy a BW far in excess of the minimum BW necessary
to transmit it. This has the effect of making the transmitted signal a noise like
appearance so as to blend into the background. Therefore Spread Spectrum is a
method of ‘camouflaging’ the information – bearing signal.
Let { bK} denotes a binary data sequence.
{ cK } denotes a PN sequence.
b(t) and c(t) denotes their NRZ polar representation respectively.
The desired modulation is achieved by applying the data signal b(t) and PN signal
c(t) to a product modulator or multiplier. If the message signal b(t) is narrowband and
the PN sequence signal c(t) is wide band, the product signal m(t) is also wide band. The
PN sequence performs the role of a ‘SpreadingCode”.
For base band transmission, the product signal m(t) represents the transmitted
signal. Therefore m(t) = c(t).b(t)
The received signal r(t) consists of the transmitted signal m(t) plus an additive
interference noise n(t), Hence
r(t) = m(t) + n(t)
= c(t).b(t) + n(t)
To recover the original message signal b(t), the received signal r(t) is applied to a
demodulator that consists of a multiplier followed by an integrator and a decision device.
The multiplier is supplied with a locally generated PN sequence that is exact replica of
that used in the transmitter. The multiplier output is given by
Z(t) = r(t).c(t)
= [b(t) * c(t) + n(t)] c(t) = c2
(t).b(t) + c(t).n(t)
The data signal b(t) is multiplied twice by the PN signal c(t), where as unwanted
signal n(t) is multiplied only once. But c2
(t) = 1, hence the above equation reduces to
Z(t) = b(t) + c(t).n(t)
Now the data component b(t) is narrowband, where as the spurious component
c(t)n(t) is wide band. Hence by applying the multiplier output to a base band (low pass)
filter most of the power in the spurious component c(t)n(t) is filtered out. Thus the effect
of the interference n(t) is thus significantly reduced at the receiver output.
The integration is carried out for the bit interval 0 ≤ t ≤ Tb to provide the sample
value V. Finally, a decision is made by the receiver.
If V > Threshold Value ‘0’, say binary symbol ‘1’ If V < Threshold Value ‘0’, say
binary symbol ‘0’
Direct – Sequence Spread Spectrum with coherent binary Phase shift
Keying:-
To provide band pass transmission, the base band data sequence is multiplied
by a Carrier by means of shift keying. Normally binary phase shift keying (PSK) is used
because of its advantages. The transmitter first converts the incoming binary data
sequence {bk} into an NRZ waveform b(t), which is followed by two stages of
modulation.
The first stage consists of a multiplier with data signal b(t) and the PN signal c(t)
as inputs. The output of multiplier is m(t) is a wideband signal. Thus a narrow – band
data sequence is transformed into a noise like wide band signal.
The second stage consists of a binary Phase Shift Keying (PSK) modulator.
Which converts base band signal m(t) into band pass signal x(t). The transmitted signal
x(t) is thus a direct – sequence spread binary PSK signal. The phase modulation θ(t) of
x(t) has one of the two values ‘0’ and ‘π’ (180o
) depending upon the polarity of the
message signal b(t) and PN signal c(t) at time t.
Polarity of PN & Polarity of PN signal both +, + or - - Phase ‘0’
Polarity of PN & Polarity of PN signal both +, - or - + Phase ‘π’
The receiver consists of two stages of demodulation.
In the first stage the received signal y(t) and a locally generated carrier are
applied to a coherent detector (a product modulator followed by a low pass filter), Which
converts band pass signal into base band signal.
The second stage of demodulation performs Spectrum despreading by
multiplying the output of low-pass filter by a locally generated replica of the PN signal
c(t), followed by integration over a bit interval Tb and finally a decision device is used to
get binary sequence.
Fig : Direct Sequence Spread Spectrum Example
Fig : Direct Sequence Spread Spectrum Using BPSK Example
Signal Space Dimensionality and Processing Gain
Fundamental issue in SS systems is how much protection spreading can
provide against interference.
SS technique distribute low dimensional signal into large dimensional signal
space (hide the signal).
Jammer has only one option; to jam the entire space with fixed total power or
to jam portion of signal space with large power.
Consider set of orthonormal basis functions;
= 2 cos 2 ≤ ≤ + 1
0
= 2 sin 2 ≤ ≤ + 1
0
= 0,1… … … … … − 1
Where Tc is chip duration, N is number of chips per bit.
Transmitted signal x(t) for the interval of an information bit is
= ( ) ( )
= ±
2 c(t)cos 2
N−1
= ± ck φk (t) 0 ≤ ≤
k=0
where, Eb is signal energy per bit.
PN Code sequence { c0, c1, ……cN-1} with ck= + 1, Transmitted signal x(t) is
therefore N dimensional and requires N orthonormal functions to represent it. j(t)
represent interfering signal (jammer). As said jammer tries to places all its available
energy in exactly same N dimension signal space. But jammer has no knowledge
of signal phase. Hence tries to place equal energy in two phase coordinates that is
cosine and sine. As per that jammer can be represented as
= −1 + -1 0 ≤ ≤
=0 =0
Where
=0 = 0,1, …?…? − 1
= 0 0,1, …?…? −1
Thus j(t) is 2N dimensional, twice the dimension as that of x(t).
Average interference power of j(t)
= 1 _ 2 = 1 _ -1 2 + 1__ -1 2
0 =0 =0
as jammer places equal energy in two phase coordinates , hence
-1 -1
2 = 2
=0 =0
-1
=2___ 2
=0
To evaluate system performance we calculate SNR at input and output of DS/BPSK
receiver. The coherent receiver input is u(t) =s(t) + c(t)j(t) and using this u(t), output at
coherent receiver
2
=
Tb
u(t) cos 2 = +
0
Where vs is despread component of BPSK and vcj of spread interference.
=
2
Tb
s(t) cos 2
02
=
Tb
c t j(t) cos 2
0
Consider despread BPSK signal s(t)
( ) = ±
2
cos 2 0 ≤? ≤
Where + sign is for symbol 1
- sign for symbol 0.
If carrier frequency is integer multiple of 1 / Tb , we have = ±
Consider spread interference component vcj, here c(t) is considered in sequence form
{ c0, c1, ……cN-1}
=
N
−1
C
=
N
−1
C
k
k=0
0
k
k=0
With Ck treated as independent identical random variables with both symbols having
equal probabilities
1
= 1 =
= −1 = 2
Expected value of Random variable vcj is zero, for fixed k we have
And Variance
| = = 1 − = −1 =
1
2
−
1
2 = 0
−
1
| =1
2
=
Spread factor N = Tb/Tc
Output signal to noise ratio is
2
=0
( ) = 2The average signal power at receiver input is Eb/Tb hence input SNR
(
) =
( )0 =
2
(
)
Expressing SNR in decibels
10 10 ( )0 = 10
10 (
) + 3 + 10 10 ,
Where =
3db term on right side accounts for gain in SNR due to coherent detection. Last term
accounts for gain in SNR by use of spread spectrum. PG is called Processing Gain.
1. Bit rate of binary data entering the transmitter input is = 1_
2. The bandwidth of PN sequence c(t) , of main lobe is Wc = 1_
=---
Probability of error
To calculate probability of error, we consider output component v of coherent
detector as sample value of random variable
= ± +
Eb is signal energy per bit and Vcj is noise component
Decision rule is, if detector output exceeds a threshold of zero volts; received bit is
symbol 1 else decision is favored for zero.
• Average probability of error Pe is nothing but conditional probability which
depends on random variable Vcj.
• As a result receiver makes decision in favor of symbol 1 when symbol 0
transmitted and vice versa
• Random variable Vcj is sum of N such random variables. Hence for
Large N it can assume Gaussian distribution.
• As mean and variance has already been discussed , zero mean and variance
JTc/2
Probability of error can be calculated from simple formula for DS/BPSK system
___
≅ 1/2 __
Antijam Characteristics
Consider error probability of BPSK
=
Comparing both probabilities;
Since bit energy Eb =PTb , P= average signal power.
We can express bit energy to noise density ratio as0
Or
The ratio J/P is termed jamming margin. Jamming Margin is expressed in decibels as
=
Where ~0 is minimum bit energy to noise ration needed to support a prescribed
average probability of error.
Example1
A pseudo random sequence is generated using a feed back shift register of
length m=4. The chip rate is 107 chips per second. Find the following
a) PN sequence length b) Chip duration of PN sequence c) PN sequence
period
Solution
a) Length of PN sequence N = 2^m-1= 2^4-1 =15
b) Chip duration Tc = 1/chip rate =1/107 = 0.1µsec
c) PN sequence period T = NTc
= 15 x 0.1µ sec = 1.5µ sec
Example2
A direct sequence spread binary phase shift keying system uses a feedback
shift register of length 19 for the generation of PN sequence. Calculate the
processing gain of the system.
Solution
Given length of shift register = m =19
Therefore length of PN sequence N = 2^m
- 1
= 2^19
- 1
Processing gain PG = Tb/Tc =N in db =10log10N = 10 log10 (2
^19) = 57db
Example3
A Spread spectrum communication system has the following parameters.
Information bit duration Tb = 1.024 msecs and PN chip duration of 1µsecs. The
average probability of error of system is not to exceed 10-5
. calculate a) Length of
shift register b) Processing gain c) jamming margin
Solution
Processing gain PG =N= Tb/Tc =1024
corresponding length of shift register m = 10
In case of coherent BPSK For Probability of error 10-5. [Referring to error function table]
Eb/N0 =10.8
Therefore jamming margin
=
− 10 10
0
= 10 10 − 10
10
0
= 10 101024 − 10 1010.8
= 30.10 − 10.33 = 19.8
Frequency – Hop Spread Spectrum:
In a frequency – hop Spread – Spectrum technique, the spectrum of data
modulated carrier is widened by changing the carrier frequency in a pseudo – random
manner. The type of spread – spectrum in which the carrier hops randomly form one
frequency to another is called Frequency – Hop (FH) Spread Spectrum.
Since frequency hopping does not covers the entire spread spectrum
instantaneously. We are led to consider the rate at which the hop occurs. Depending
upon this we have two types of frequency hop.
1. Slow frequency hopping:- In which the symbol rate Rs of the MFSK signal is an
integer multiple of the hop rate Rh. That is several symbols are transmitted on
each frequency hop.
2. Fast – Frequency hopping:- In which the hop rate Rh is an integral multiple of the
MFSK symbol rate Rs. That is the carrier frequency will hoop several times
during the transmission of one symbol. A common modulation format for
frequency hopping system is that of M- ary frequency – shift – keying (MFSK).
Slow frequency hopping:-
Fig Shows the block diagram of an FH / MFSK transmitter, which involves
frequency modulation followed by mixing.
The incoming binary data are applied to an M-ary FSK modulator. The resulting
modulated wave and the output from a digital frequency synthesizer are then applied to
a mixer that consists of a multiplier followed by a band – pass filter. The filter is
designed to select the sum frequency component resulting from the multiplication
process as the transmitted signal. An ‘k’ bit segments of a PN sequence drive
the frequency synthesizer, which enables the carrier frequency to hop over 2
^n
distinct values. Since frequency synthesizers are unable to maintain phase
coherence over successive hops, most frequency hops spread spectrum
communication system use non coherent M-ary modulation system.
Fig :- Frequency hop spread transmitter
Fig :- Frequency hop spread receiver
In the receiver the frequency hopping is first removed by mixing the received
signal with the output of a local frequency synthesizer that is synchronized with the
transmitter. The resulting output is then band pass filtered and subsequently processed
by a non coherent M-ary FSK demodulator. To implement this M-ary detector, a bank of
M non coherent matched filters, each of which is matched to one of the MFSK tones is
used. By selecting the largest filtered output, the original transmitted signal is estimated.
An individual FH / MFSK tone of shortest duration is referred as a chip. The chip
rate Rc for an FH / MFSK system is defined by
Rc = Max(Rh,Rs)
Where Rh is the hop rate and Rs is Symbol Rate
In a slow rate frequency hopping multiple symbols are transmitted per hop.
Hence each symbol of a slow FH / MFSK signal is a chip. The bit rate Rb of the
incoming binary data. The symbol rate Rs of the MFSK signal, the chip rate Rc and the
hop rate Rn are related by
Rc = Rs = Rb /k ≥ Rh
where k= log2M
Fast frequency hopping:-
A fast FH / MFSK system differs from a slow FH / MFSK system in that
there are multiple hops per m-ary symbol. Hence in a fast FH / MFSK system each hop
is a chip.
Fast Frequency Hopping Slow Frequency Hopping
Several frequency hops Per modulation
Several modulation symbols per hop
Shortest uninterrupted waveform
Shortest uninterrupted waveformin
in the system is that of hop
the system is that of data symbol
Chip duration =hop duration Chip duration=bit duration.
The following figure illustrates the variation of the frequency of a slow FH/MFSK
signal with time for one complete period of the PN sequence. The period of the PN
sequence is 24-1 = 15.
The FH/MFSK signal has the following parameters:
Number of bits per MFSK symbol K = 2. Number of MFSK tones M = 2
^K = 4
Length of PN segment per hop k = 3; Total number of frequency hops 2
^k = 8
Fig. Slow frequency hopping
The following figure illustrates the variation of the transmitted frequency of a fast
FH/MFSK signal with time.
The signal has the following parameters:
Number of bits per MFSK symbol K = 2. Number of MFSK tones M = 2
K = 4
Length of PN segment per hop k = 3; Total number of frequency hops
2
k = 8
Fig. Fast frequency hopping
FHSS Performance Considerations:
• Typically large number of frequencies used
– Improved resistance to jamming
Code Division Multiple Access (CDMA):
• Multiplexing Technique used with spread spectrum
• Start with data signal rate D
– Called bit data rate
• Break each bit into k chips according to fixed pattern specific to each user
– User’s code
• New channel has chip data rate kD chips per second
• E.g. k=6, three users (A,B,C) communicating with base receiver R
• Code for A = <1,-1,-1,1,-1,1>
• Code for B = <1,1,-1,-1,1,1>
• Code for C = <1,1,-1,1,1,-1>
CDMA Example:
• Consider A communicating with base
• Base knows A’s code
• Assume communication already synchronized
• A wants to send a 1
– Send chip pattern <1,-1,-1,1,-1,1>
• A’s code
• A wants to send 0
– Send chip[ pattern <-1,1,1,-1,1,-1>
• Complement of A’s code
• Decoder ignores other sources when using A’s code to decode
– Orthogonal codes
–
CDMA for DSSS:
• n users each using different orthogonal PN sequence
• Modulate each users data stream
– Using BPSK
• Multiply by spreading code of user
CDMA in a DSSS Environment:
QUESTIONS FOR PRACTISE
Part A
1. Define constraint length in convolutional codes?
2. What is pseudo noise sequence?
3. What is direct sequence spread spectrum modulation
4. What is frequency hap spread spectrum modulation?
5. What is processing gain?
6. What is jamming margin ?
7. When is the PN sequence called as maximal length sequence?
8. What is meant by processing gain of DS spread spectrum system?
9. What is the period of the maximal length sequence generated using 3 bit shift
register.
10. Define frequency hopping.
11. What are the Advantages of DS-SS system
12. What are the Disadvantages of DS-SS system.
13. What are the Advantages of FH-SS System
14. What are the Disadvantages of FH-SS System15. Define synchronization in Spread Spectrum Systems
16. Comparison between DS-SS and FH-SS
17. What are the Application of Direct Sequence Spread Spectrum
18. State the balance property of random binary sequence.
19. Mention about the run property.
20. What is called jamming effect.
21. What is Anti jamming ?
22. What is slow and fast frequency hopping.
23. What is called multipath Interference?
PART B
1. What is Spread Spectrum Techniques Explain in detail about Direct
Sequence Spread Spectrum Techniques with necessary diagrams?
i. Concept of Spread Spectrum Techniques
ii. Block Diagram Representation.
iii.Waveform at all stages of the system.
iv. Derivation of processing Gain.
2. What is Frequency Hopping? Explain the different types of frequency hopping
with necessary diagrams.
i. Concept of frequency hopping.
ii. Explanation of slow frequency hopping
iii.Explanation of Fast frequency hopping
iv. Block Diagrams and waveform
******************************************************************************
******************************************************************************
Explain various Multiplexing Techniques.
Frequency Division Multiple Access (FDMA)
It is one of the most common multiplexing procedures. FDMA is a channel access technique
found in multiple-access protocols as a channelization protocol.
FDMA permits individual allocation of single or multiple frequency bands, or channels to the
users.
Figure 12: Frequency Division Multiple Access
FDMA permits multiple users to simultaneously access a transmission system.
In FDMA, every user shares the frequency channel or satellite transpondersimultaneously;
however, every user transmits at single frequency
FDMA is compatible with both digital and analog signals.
FDMA demands highly efficient filters in the radio hardware, contrary to CDMA and TDMA.
FDMA is devoid of timing issues that exist in TDMA.
As a result of the frequency filtering, FDMA is not prone to the near-far problem that exists in
CDMA.
All users transmit and receive at different frequencies because every user receives an individual
frequency slot.
One disadvantage of FDMA is crosstalk, which can cause interference between frequencies and
interrupt the transmission.
Space Division Multiple Access (SDMA)
SDMA utilizes the spatial separation of the users in order to optimize the use of the frequency
spectrum.
A primitive form of SDMA is when the same frequency is reused in different cells in a cellular
wireless network.
The radiated power of each user is controlled by Space division multiple access.
SDMA serves different users by using spot beam antenna. These areas may be served by the
same frequency or different frequencies.
However for limited co-channel interference it is required that the cells are sufficiently
separated. This limits the number of cells a region can be divided into and hence limits the
frequency re-use factor. A more advanced approach can further increase the capacity of the
network. This technique would enable frequency re-use within the cell. In a practical cellular
environment it is improbable to have just one transmitter fall within the receiver beam width.
Therefore it becomes imperative to use other multiple access techniques in conjunction with
SDMA.
Figure 1: Space Division Multiple Access
When different areas are covered by the antenna beam, frequency can be re-used, in which
case TDMA or CDMA is employed, for different frequencies FDMA can be used.
Time Division Multiple Access (TDMA)
It is a multiplexing technique where multiple channels are multiplexed over time.
In TDMA, several users share the same frequency channel of higher bandwidth by dividing the
signal into different timeslots.
Users transmit their data using their own respective time slots in rapid succession; to
synchronize, the transmitter and the receiver need to synchronize using a global clock.
It is divided into two types:-
Fixed TDMA
In this, connections between time slots in each frame and data streams assigned to a user
remain static and switched only when large variations in traffic are required.
In this variant, the slot sizes are fixed atT/N (T is time in seconds and N is the number of users).
Dynamic TDMA
Figure 2: Time Division Multiple Access
In this, a scheduling algorithm is used to dynamically reserve a variable number of time slots in
each frame to variable bit-rate data streams.
This reservation algorithm is based on the traffic demand of each data stream.
Code Division Multiple Access (CDMA)
Short for Code-Division Multiple Access, a digital cellular technology that uses spread-spectrum
techniques. It is a broadband system.
CDMA uses spread spectrum technique where each subscriber uses the whole system
bandwidth.Figure 3: Code Division Multiple Access
Unlike competing systems, such as GSM, that use TDMA, CDMA does not assign a specific
frequency to eachuser.
Instead, every channel uses the full available spectrum. Individual conversations are encoded
with a pseudo-random digital sequence.
CDMA consistently provides better capacity for voice and data communications than other
commercialmobiletechnologies,allowing moresubscriberstoconnectatanygiventime,andit
is the common platform on which 3G technologies are built.
For example, CDMA is a military technology first used during World War II by English allies to
foil German attempts at jamming transmissions.
Unlike the FDMA or TDMA where a frequency or time slot is assigned exclusively to a
subscriber,inCDMAall subscribers ina celluse thesamefrequencyband simultaneously.
To separate the signals, each subscriber is assigned an orthogonal code called “chip”.
4. Define various mobile computing functions.
The mobile computing functions can be divided into the following major segments:-
User with Device
This means that this could be a fixed device like a desktop computer in an office or a portable
device like mobile phone. Example: Laptop computers, desktop computers, fixed telephone,mobile phones, digital TV with set-top box, palmtop computers, pocket PCs, two-way pagers,
handheld terminals, etc.
Network
Figure 16: Mobile Computing Functions
Whenever a user is using a mobile, he will use different networks at different locations at
different times. Example: GSM, CDMA, iMode, Ethernet,Wireless LAN,Bluetooth, etc.
Gateway
This acts as an interface between different transports bearers. These gateways convert one
specific transport bearer toanother.
Example, from a fixed phone we access a service by pressing different keys on the telephone.
These key generates DTMF (Dual Tone Multi Frequency).
These analog signals are converted into digital data by the IVR (Interactive Voice Response)
gateway to interface with a computer application.
Middleware
This is more of a function rather than a separate visible node. In the present context,
middleware handles the presentation and rendering of the content on a particular device.
It may optionally also handle the security and personalization for different users.
Content
This is the domain where the origin server and content is. This could be an application, system,
or even an aggregation of systems.
The content can be mass market, personal or corporate content. The origin server will have
some means of accessing the database and storage devices.
Explain design consideration for mobile computing.
Mobile computing is basically the use of portable devices that are capable of use wireless
network communication.
It is divided into mobile devices and wireless communication.
For designing mobile applications have altogether different challenges than designing desktop
application. It requires different mind-set.
On mobile platform everything is limited to make balance between design principles and
resources at hand such changes shall mean that content and behavior of applications should be
adapted to suit the current situation.
Few of design consideration parameter for mobile computing:
Native vs. Mobile Web
If your application requires local processing, access to local resources and can work in
occasionally connected scenario or no connectivity consider designing a native application.
A native application is hard to maintain, requires separate distribution and upgrade
infrastructure, are compatible only with target device/platform, requires more effort
(sometimes huge) to port on different devices.
A mobile web application is compatible with all devices with internet connection and a browser.
Target device
Target device and platform (OS) play a key role throughout design decisionsmaking process.
Design decisions are influenced by target device’s screen size, resolution, orientations, memory,
CPU performance characteristics, Operating systems capabilities, OEM (device vendor) specific
OS changes/limitations, device hardware, user input mechanism (touch/non-touch), sensors
(such as GPS or accelerometer) etc.
User experience
User experience, for mobile applications, needs utmost importance (may be more than
desktop).
User interface should be rich, intuitive and responsive. While using mobile application user is
often distracted by external or internal (e.g. incoming call when user is in middle of a wizard)
events.
Resource Constraint
In design decision should take into account the limited CPU, memory and battery life.
Reading and writing to memory, wireless connections, specialized hardware, and processor
speed all have an impact on the overall power usage.
For example using notification or app directedSMSinstead of polling to monitor a value/flag on
server.
Multiple Platform
An application will target not only one platform or only one device.
In near future, requirement like same code base should support iPhone and iPad or Android
Phone and Android tablet will arise.
Design Architect should consider portability, technology agnostic with platform specific
implementation. To make design with reuse across the platforms.
Security
Devices are more vulnerable than desktop, primarily due to lack of awareness.
It may device can be lost easily. It needs to secureddevice – server communication and server
accepts request only from authentic source (device).
If you are storing any confidential application or configuration data locally, ensure that the data
is encrypted.
Network Communication
Network communication on device is very significant parameter.
To reduce network traffic by combining several commands in one request.
For example, committing added, updated and deleted records in one request instead of firing
separate request on each add/update/delete.
Explain the differences between 1G, 2G, 2.5G and 3G mobile
communications.
1G
It is the first generation cellular network that existed in 1990’s.
It transfer data in analog wave, it has limitation because there are no encryption, the sound
quality is poor and the speed of transfer is only 9.6 kbps.
2G
It is the second generation, improved by introducing the concept of digital modulation, which
means converting the voice into digital code and then into analog signals.
Being over limitation 1G, such as it omits the radio power from handsets making life healthier,
and it has enhancedprivacy.
2.5G
It is a transition of 2G and 3G.
In 2.5G, the most popular services like SMS, GPRS, EDGE, high speed circuit switched data and
more had beenintroduced.
3G
It is the current generation of mobile telecommunication standards.
It allows use of speech and data services and offers data rates up to 2 mbps, which provide
services like video calls, mobile TV, mobile internet and downloading.
There are bunch of technologies that fall 3G, likeWCDMA, EV-DO, and HSPA etc.
4G
It is the fourth generation of cellular wireless standards. It is a successor to the 3G and 2G
families of standards.
In 2008, the ITU-R organization specifies the IMT Advanced (International Mobile
Telecommunication Advanced) requirements for 4G standards, setting peak speed requirements for 4G service at 100 Mbit/s for high mobility communication and 1 Gbit/s for low mobility communication.
4G system
It is expected to provide a comprehensive and secure all-IP based mobile broadband solution to
laptop computer wireless modems, smart phones, and other mobile devices.
Gen. Definition Throughput/Speed Technology Features
1G
Analog 14.4 Kbps\ AMPS,NMT,
During 1G Wireless phones are
(1970 to
(peak)
TACS
used for voiceonly.
1980)
2G
Digital
9.6/14.4 TDMA,CDMA 2G capabilities are achieved by
(1990 to
Narrow band
Kbps
allowing multiple users on a single
2000)
circuit data
channel via multiplexing
During 2G Cellular phones are used
for data also along with voice.
.
2.5G
Packet Data 171.2 GPRS In 2.5G the internet becomes
popular and
(2001 to
Kbps(peak) data becomes more
relevant.2.5G Multimedia
2004)
20-40 Kbps services and streaming starts to show growth
Phones start supporting web
browsing through limited and very
few phones have that.
.
3G
Digital 3.1 Mbps
CDMA 20 3G has Multimedia services support
(2004 to
Broadband
(peak)
(1xRTT, along with streaming are more
2005)
Packet Data 500-700
Kbps
EVDO) popular.In 3G, Universal access and
UMTS, EDGE
portability across different device
types are made possible.
(Telephones, PDA’s, etc.)
3.5G
Packet Data 14.4 Mbps HSPA 3.5G supports higher throughput
(2006 to (peak) and speeds to support higher data
2010)
1-3 Mbps needs of the consumers
.
4G
Digital
100-300 WiMax Speeds for 4G are further increased
(Now
Broadband Mbps (peak)
LTE to keep up with data access
(Read
Packet 3-5 Mbps Wi-Fi demand used by various services.
more on
All IP 100 Mbps
High definition streaming is now
Transition
Very high (Wi-Fi)
supported in 4G. New phones with
ingto4G)
throughput
HD capabilities surface. It gets pretty cool.
In 4G, Portability is increased
further. World-wide roaming is not
a distant dream.
Facilities such as ultra-broadband Internet
access, IP telephony, gaming services and
streamed multimedia may be provided to users.
PRE-4G
This technology such asmobileWiMax and Long term evolution (LTE) has been on
the market since 2006 and 2009 respectively, and are often branded as 4G.
*** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ****************************************************
.
DECT DIGITAL ENHANCED CORDLESS TELECOMMUNICATION
BACKGROUND INFORMATION AND HISTORY
FUNCTIONALITY
USAGE IN SOCIETY
************************************************************************************* *************************************************************************************
GSM ARCHITECTURE
CONTENT
NETWORK STRUCTURE
MOBILE EQUIPMENT
SUBSCRIBER IDENTITY MODULE
NETWORK SWITCHING SUBSYSTEM
HOME LOCATION REGISTER
VISITORS LOCATION REGISTER
EQUIPMENT IDENTITY REGISTER OPERATION AND MAINTENANCE CENTER ************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************************
GSM Architecture
The GSM network comprises of many functional units, this function and interface are explained in this
part. The GSM network can be broadly divided into
1. Mobile Station (MS)
2. the Base Station Subsystem (BSS)
3. The network switching Subsystem(NSS)
4. Operation Support subsystem(OSS)
Mobile Station (MS)
the MS consist of Physical Equipment such as the Radio transiver, display, digital signal
processor and SIM Card . The MS Also provides access to the various data services avaliable in
GSM network. These data services include:
1. X.25 packet switching through a synchronous or Asynchronous dialog connection to the
PAD(Portable access device) at speed tipically at 9.6 kbps.
2. General Packet Radio Service(GPRS) using IP based data transfer method at the speed upto 115
kbps
3. High Speed Circuit Switch Data at speed upto 64kbps
Base Station SubSystem (BSS)
The BSS is composed of two parts
1. The base transiver station (BTS)
2. Base station Controller (BSC)
BTS
the BTS houses the radio transivers that defines a cell and handles the radio link protocol with the MS.
Each BTS serves as a single cell.
It also includes the following functinos
1. Encoding, Encrypting, Multiplexing, Modulating and Feeding the RF signal to the antina.
2. Transcoding and Data Adoptation
3. Time and Frequency Synchronizing4. Decoding, Decryption, Equilizing Recived Signal, Uplink Channel Messurement
BSC
The BSC manages the radio resource for one or more BTS. It handle radio channel setup, Frquency
Hopping and handover. The BSC is the connection between the mobile and MSC. The Additional
Functions include:
1. Control of frequency Hopping
2. Performing traffic concentration to reduce the number of lines from the MSC
3. Providing an Interface to an operations and maintenance center for the BSS
4. Power Management
5. Time and Frequency Synchronization
*************************************************************************
**************************************************************************
CDMA TDMA FDMA
DIFFERENCE BETWEEN MULTIPLE
ACCESS AND MULTIPLEXING
FREQUENCY DIVISION MULTIPLE
ACCESS (FDMA)
HOW IT WORKS?
DIFFERENCE BETWEEN FDMA AND FDM
DISADVANTAGES OF FDMA
TIME DIVISION MULTIPLE ACCESS
(TDMA)
FDMA VS TDMA
CDMA VS TDMA
ADVANTAGES
DISADVANTAGES
CODE DIVISION MULTIPLE ACCESS
(CDMA)
ADVANTAGES
DISADVANTAGES
WORKING OF CDMA
APPLICATIONS OF CDMA TECHNOLOGY
****************************************
****************************************
Spread Spectrum
Introduction to Spread Spectrum Spread Spectrum Criteria
Spread Spectrum Background
How Spread Spectrum Works
PN Sequences
Spread Spectrum Classification
Direct Sequence Spread Spectrum
(DSSS)
Direct Sequence Spread Spectrum Example
Direct Sequence Spread Spectrum:
Transmission Technique
Direct Sequence Spread Spectrum
Transmitter
Direct Sequence Spread Spectrum
Receiver
Frequency Hopping Spread Spectrum
(FHSS)
******************************************************************************************
WIRELESS COMMUNICATION – SATELLITE
A satellite is an object that revolves around another object. For example, earth is a
satellite of The Sun, and moon is a satellite of earth.
A communication satellite is a microwave repeater station in a space that is used for
telecommunication, radio and television signals. A communication satellite processes the data
coming from one earth station and it converts the data into another form and send it to the
second earth station.
Two stations on earth want to communicate through radio broadcast but are too far away
to use conventional means. The two stations can use a relay station for their communication.
One earth station transmits the signal to the satellite.
Uplink frequency is the frequency at which ground station is communicating with
satellite. The satellite transponder converts the signal and sends it down to the second earthstation, and this is called Downlink frequency. The second earth station also communicates with the
first one in the same way.
ADVANTAGES OF SATELLITE
The advantages of Satellite Communications are as follows −
The Coverage area is very high than that of terrestrial systems.
The transmission cost is independent of the coverage area.
Higher bandwidths are possible.
DISADVANTAGES OF SATELLITE
The disadvantages of Satellite Communications are as follows −
Launching satellites into orbits is a costly process.
The bandwidths are gradually used up.
High propagation delay for satellite systems than the conventional terrestrial systems.
SATELLITE COMMUNICATION BASICS
The process of satellite communication begins at an earth station. Here an installation is
designed to transmit and receive signals from a satellite in orbit around the earth. Earth stations
send information to satellites in the form of high powered, high frequency (GHz range) signals.
The satellites receive and retransmit the signals back to earth where they are received
by other earth stations in the coverage area of the satellite. Satellite's footprint is the area
which receives a signal of useful strength from the satellite.
The transmission system from the earth station to the satellite through a channel is called
the uplink. The system from the satellite to the earth station through the channel is called
the downlink.
SATELLITE FREQUENCY BANDS
The satellite frequency bands which are commonly used for communication are
the Cband, Ku-band, and Ka-band. C-band and Ku-band are the commonly used frequency
spectrums by today's satellites.
It is important to note that there is an inverse relationship between frequency and
wavelength i.e. when frequency increases, wavelength decreases this helps to understand therelationship between antenna diameter and transmission frequency. Larger antennas
(satellite dishes) are necessary to gather the signal with increasing wavelength.
EARTH ORBITS
A satellite when launched into space, needs to be placed in certain orbit to provide a
particular way for its revolution, so as to maintain accessibility and serve its purpose whether
scientific, military or commercial. Such orbits which are assigned to satellites, with respect to
earth are called as Earth Orbits. The satellites in these orbits are Earth Orbit Satellites.
The important kinds of Earth Orbits are −
Geo-synchronous Earth Orbit
Geo-stationary Earth Orbit
Medium Earth Orbit
Low Earth Orbit
Geo-synchronous Earth Orbit (GEO) Satellites
A Geo-synchronous Earth orbit Satellite is one which is placed at an altitude of 22,300
miles above the Earth. This orbit is synchronized with a side real day (i.e., 23hours 56minutes).
This orbit can have inclination and eccentricity. It may not be circular. This orbit can be tilted
at the poles of the earth. But it appears stationary when observed from the Earth.
The same geo-synchronous orbit, if it is circular and in the plane of equator, it is called
as geo-stationary orbit. These Satellites are placed at 35,900kms (same as geosynchronous)
above the Earth’s Equator and they keep on rotating with respect to earth’s direction (west to
east). These satellites are considered stationary with respect to earth and hence the name
implies.
Geo-Stationary Earth Orbit Satellites are used for weather forecasting, satellite TV,
satellite radio and other types of global communications.FIGURE -GEO-SYNCHRONOUS
The above figure shows the difference between Geo-synchronous and Geo- Stationary
orbits. The Axis of rotation indicates the movement of Earth.
The main point to note here is that every Geo-Stationary orbit is a Geo-Synchronous
orbit. But every Geo-Synchronous orbit is NOT a Geo-stationary orbit.
Medium Earth Orbit (MEO) Satellites
Medium earth orbit (MEO) satellite networks will orbit at distances of about 8000 miles
from earth's surface. Signals transmitted from a MEO satellite travel a shorter distance. This
translates to improved signal strength at the receiving end. This shows that smaller, more
lightweight receiving terminals can be used at the receiving end.
Since the signal is travelling a shorter distance to and from the satellite, there is less
transmission delay. Transmission delay can be defined as the time it takes for a signal to travel
up to a satellite and back down to a receiving station.
For real-time communications, the shorter the transmission delay, the better will be the
communication system. As an example, if a GEO satellite requires 0.25 seconds for a round
trip, then MEO satellite requires less than 0.1 seconds to complete the same trip. MEOs
operates in the frequency range of 2 GHz and above.Low Earth Orbit (LEO) Satellites
The LEO satellites are mainly classified into three categories namely, little LEOs, big
LEOs, and Mega-LEOs. LEOs will orbit at a distance of 500 to 1000 miles above the earth's
surface.
This relatively short distance reduces transmission delay to only 0.05 seconds. This
further reduces the need for sensitive and bulky receiving equipment. Little LEOs will operate
in the 800 MHz (0.8 GHz) range. Big LEOs will operate in the 2 GHz or above range, and
Mega-LEOs operates in the 20-30 GHz range.
The higher frequencies associated with Mega-LEOs translates into more information
carrying capacity and yields to the capability of real-time, low delay video transmission scheme.
High Altitude Long Endurance (HALE) Platforms
Experimental HALE platforms are basically highly efficient and lightweight airplanes
carrying communications equipment. This will act as very low earth orbit geosynchronous
satellites.
These crafts will be powered by a combination of battery and solar power or high
efficiency turbine engines. HALE platforms will offer transmission delays of less than 0.001
seconds at an altitude of only 70,000 feet, and even better signal strength for very lightweight
hand-held receiving devices.
Orbital Slots
Here there may arise a question that with more than 200 satellites up there in
geosynchronous orbit, how do we keep them from running into each other or from attempting to
use the same location in space? To answer this problem, international regulatory bodies like the
International Telecommunications Union (ITU) and national government organizations like the
Federal Communications Commission (FCC) designate the locations on the geosynchronous
orbit where the communications satellites can be located.
These locations are specified in degrees of longitude and are called as orbital slots. The
FCC and ITU have progressively reduced the required spacing down to only 2 degrees for C�
band and Ku-band satellites due to the huge demand for orbital slots.
************************************************************************************************************************************
************************************************************************************************************************************
WIRELESS NETWORKS
Presentation Outline
• Wireless Technology overview
• The IEEE 802.11 WLAN Standards
• Secure Wireless LANs
• Migrating to Wireless LANs (Cutting the cord)
Wireless?
• A wireless LAN or WLAN is a wireless local area network that uses radio waves as its carrier.
• The last link with the users is wireless, to give a network connection to all users in a building or campus.
• The backbone network usually uses cables
Common Topologies
The wireless LAN connects to a wired LAN
• There is a need of an access point that bridges wireless LAN traffic into the
wired LAN.
• The access point (AP) can also act as a repeater for wireless nodes,
effectively doubling the maximum possible distance between nodes.
Common Topologies
Complete Wireless Networks
• The physical size of the network is determined by the maximum reliable propagation range of the radio signals.
• Referred to as ad hoc networks
• Are self-organizing networks without any centralized control
• Suited for temporary situations such as meetings and conferences.
How do wireless LANs work?
Wireless LANs operate in almost the same way as wired LANs, using the same networking protocols and supporting the most of the same applications.
How are WLANs Different?
• They use specialized physical and data link protocols
• They integrate into existing networks through access points which provide a bridging function
• They let you stay connected as you roam from one coverage area to another
• They have unique security considerations
• They have specific interoperability requirements
• They require different hardware
• They offer performance that differs from wired LANs.
Physical and Data Link Layers
Physical Layer:
• The wireless NIC takes frames of data from the link layer, scrambles the data in a
predetermined way, then uses the modified data stream to modulate a radio carrier
signal.
Data Link Layer:
• Uses Carriers-Sense-Multiple-Access with
Collision Avoidance (CSMA/CA).
Integration With Existing Networks
• Wireless Access Points (APs) - a small device that bridges wireless traffic to your network.
• Most access points bridge wireless LANs into Ethernet networks, but Token-Ring options are available as well.
Roaming
• Users maintain a continuous connection as they roam from one physical area to another
• Mobile nodes automatically register with the new access point.
•Methods: DHCP, Mobile IP
• IEEE 802.11 standard does not address roaming, you may need to purchase equipment from one vendor if your users need to roam from one access point to another.
Security
• In theory, spread spectrum radio signals are inherently difficult to decipher without knowing the exact hopping sequences or direct sequence codes used
• The IEEE 802.11 standard specifies optional security called "Wired Equivalent Privacy"
whose goal is that a wireless LAN offer privacy equivalent to that offered by a wired LAN. The standard also specifies optional authentication measures.
Interoperability
• Before the IEEE 802.11 interoperability was based on cooperation between vendors.
• IEEE 802.11 only standardizes the physical and medium access control layers.
• Vendors must still work with each other to ensure their IEEE 802.11 implementations interoperate
• Wireless Ethernet Compatibility Alliance (WECA) introduces the Wi-Fi Certification to ensure cross� vendor interoperability of 802.11b solutions
Hardware
• PC Card, either with integral antenna or with external antenna/RF module.
• ISA Card with external antenna connected by cable.
• Handheld terminals
• Access points
Hardware
Performance
• 802.11a offers speeds with a theoretically maximum rate of 54Mbps in the 5 GHz band
•802.11b offers speeds with a theoretically maximum rate of 11Mbps at in the 2.4 GHz
spectrum band
• 802.11g is a new standard for data rates of up to a theoretical maximum of 54 Mbps at 2.4 GHz.
What is 802.11?
• A family of wireless LAN (WLAN) specifications developed by a working group at the Institute of Electrical and Electronic Engineers (IEEE)
• Defines standard for WLANs using the following four technologies
• Frequency Hopping Spread Spectrum (FHSS)
• Direct Sequence Spread Spectrum (DSSS)
• Infrared (IR)
• Orthogonal Frequency Division Multiplexing (OFDM)
• Versions: 802.11a, 802.11b, 802.11g, 802.11e, 802.11f, 802.11i
802.11 - Transmission
• Most wireless LAN products operate in unlicensed radio bands
• 2.4 GHz is most popular
• Available in most parts of the world
• No need for user licensing
• Most wireless LANs use spread-spectrum radio
• Resistant to interference, secure
• Two popular methods
• Frequency Hopping (FH)
• Direct Sequence (DS)
Frequency Hopping Vs. Direct Sequence
• FH systems use a radio carrier that “hops” from frequency to frequency in a pattern known to both transmitter and receiver
• Easy to implement
• Resistance to noise
• Limited throughput (2-3 Mbps @ 2.4 GHz)
• DS systems use a carrier that remains fixed to a specific frequency band. The data signal is spread onto a much larger range of frequencies (at a much lower power level) using a
specific encoding scheme.
• Much higher throughput than FH (11 Mbps)
• Better range
• Less resistant to noise (made up for by redundancy – it transmits at
least 10 fully redundant copies of the original signal at the same time)
802.11a
• Employs Orthogonal Frequency Division Multiplexing (OFDM)
• Offers higher bandwidth than that of 802.11b, DSSS (Direct Sequence Spread Spectrum)
• 802.11a MAC (Media Access Control) is same as802.11b
• Operates in the 5 GHz range
802.11a Advantages
• Ultra-high spectrum efficiency
• 5 GHz band is 300 MHz (vs. 83.5 MHz @ 2.4 GHz)
• More data can travel over a smaller amount of bandwidth
• High speed
• Up to 54 Mbps
• Less interference
• Fewer products using the frequency
• 2.4 GHz band shared by cordless phones, microwave ovens, Bluetooth, and WLANs
802.11a Disadvantages
•Standards and Interoperability
• Standard not accepted worldwide
• No interoperability certification available for 802.11a products
• Not compatible or interoperable with 802.11b
• Legal issues
• License-free spectrum in 5 GHz band not available worldwide
• Market
• Beyond LAN-LAN bridging, there is limited interest for5 GHz adoption
802.11a Disadvantages
• Cost
• 2.4 GHz will still has >40% cost advantage
• Range
• At equivalent power, 5 GHz range will be ~50% of 2.4 GHz
• Power consumption
• Higher data rates and increased signal require more power
• OFDM is less power-efficient then DSSS
802.11a Applications
• Building-to-building connections
• Video, audio conferencing/streaming video,and audio
• Large file transfers, such as engineeringCAD drawings
• Faster Web acess and browsing
• High worker density or high throughput scenarios
• Numerous PCs running graphics-intensive applications
802.11a Vs. 802.11b
802.11a vs. 802.11a 802.11b
802.11b
Raw data rates Up to 54 Mbps Up to 11 Mbps
(54, 48, 36, 24,18, 12
(11, 5.5, 2, and
and 6 Mbps)
1 Mbps)
Range 50 Meters 100 Meters
Bandwidth UNII and ISM
ISM (2.4000—
(5 GHz range) 2.4835 GHz range)
Modulation OFDM technology DSSS technology
802.11g
• 802.11g is a high-speed extension to 802.11b
• Compatible with 802.11b
• High speed up to 54 Mbps
• 2.4 GHz (vs. 802.11a, 5 GHz)
• Using ODFM for backward compatibility
• Adaptive Rate Shifting
802.11g Advantages
• Provides higher speeds and higher capacity requirements for applications
• Wireless Public Access
• Compatible with existing 802.11b standard
• Leverages Worldwide spectrum availability in 2.4 GHz
• Likely to be less costly than 5 GHz alternatives
• Provides easy migration for current users of 802.11b WLANs
• Delivers backward support for existing 802.11b products
• Provides path to even higher speeds in the future
802.11e Introduces Quality of Service
• Also know as P802.11 TGe
• Purpose:
• To enhance the 802.11 Medium Access Control (MAC) to improve and manage Quality of Service (QoS)
• Cannot be supported in current chip design
• Requires new radio chips
• Can do basic QoS in MAC layer
802.11f – Inter Access Point Protocol
• Also know as P802.11 TGf
• Purpose:
• To develop a set of requirements for Inter-Access Point Protocol (IAPP), including operational and management aspects
802.11b Security Features
• Wired Equivalent Privacy (WEP) – A protocol to protect link-level data during wireless transmission between clients and access points.
• Services:
• Authentication: provides access control to the network bydenying access to client stations that fail to authenticate properly.
• Confidentiality: intends to prevent information compromise from casual eavesdropping
• Integrity: prevents messages from being modified while in
transit between the wireless client and the access point.
Authentication
Means:
• Based on cryptography
• Non-cryptographic
• Both are identity-based verification mechanisms (devices request access based on the SSID –Service Set Identifier of the wireless network).
Authentication
• Authentication techniques
Privacy
• Cryptographic techniques
• WEP Uses RC4 symmetric key, stream cipher algorithm to generate a pseudo random data sequence. The stream is XORed with the data to be transmitted
• Key sizes: 40bits to 128bits
• Unfortunately, recent attacks have shown that the WEP approach for privacy is vulnerable to certain attack regardless of key size
Data Integrity
• Data integrity is ensured by a simple encrypted version of CRC (Cyclic Redundant Check)
• Also vulnerable to some attacks
WLAN Migration – Cutting The Cord
• Essential Questions
• Choosing the Right Technology
• Data Rates
• Access Point Placement and Power
• Antenna Selection and Placement
• COnnecting to the Wired LAN
• The Site Survey
Essential Questions
• Why is the organization considering wireless?
Allows to clearly define requirements of the WLAN -> development plan
• How many users require mobility?
• What are the applications that will run over the WLAN? Helps to determine bandwidth
requirements, a criteria to choose between available technologies. Wireless is a shared
medium, not switched!!!
Choose the right technology
• Usually IEEE 802.11b or 802.11a
• 802.11b offers interoperability (WECA Wi-Fi Certification Program)
• 802.11a offers higher data rates (up to 54 mbps) -> higher throughput per user. Limite
interoperability.
Data rates
• Data rates affect range
• 802.11b 1 to 11 Mbps in 4 increments
• 802.11a 6 to 54 Mbps in 7 increments
• The minimum data rate must be determined at design time
• Selecting only the highest data rate will require a greater number of APs to cover a specific area
• Compromise between data rates and overall system cost
Access Point Placement and Power
• Typically – mounted at ceiling height.
• Between 15 and 25 feet (4.5m to 8m)
• The greater the height, the greater the difficulty to get power to the unit. Solution:
consider devices that can be powered using CAT5 Ethernet cable (CISCO Aironet 1200
Series).
• Access points have internal or external antennas
Antenna Selection and Placement
• Permanently attached.
• Remote antennas connected using an antenna cable.
•Coax cable used for RF has a high signal loss, should not be mounted more than a 1 or 2 meters away from the device.
• Placement: consider building construction, ceiling height, obstacles, and aesthetics. Different materials (cement, steel) have different radio propagation characteristics.
Connecting to the Wired LAN
• Consider user mobility
• If users move between subnets, there are challenges to consider.
• OSes like Windows XP and 2000, Linux support DHCP to obtain the new IP address for the subnet. Certain applications such as VPN will fail.
• Solution: access points in a roaming area areon the same segment.
******************************************************************
















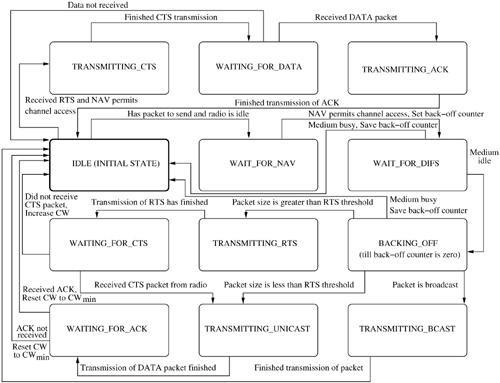






















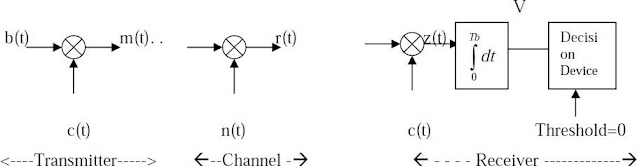




























































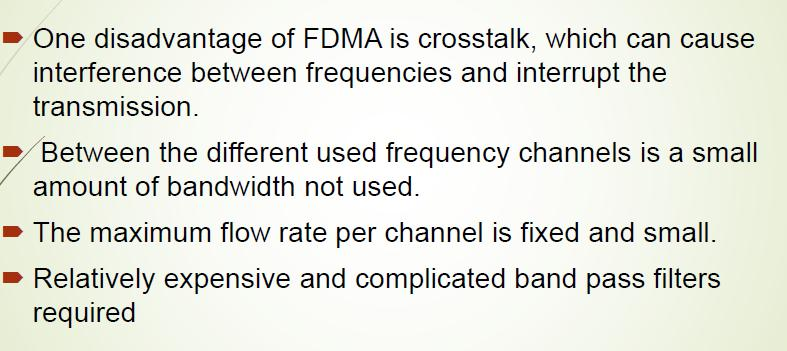











































Comments
Post a Comment